
We value your privacy
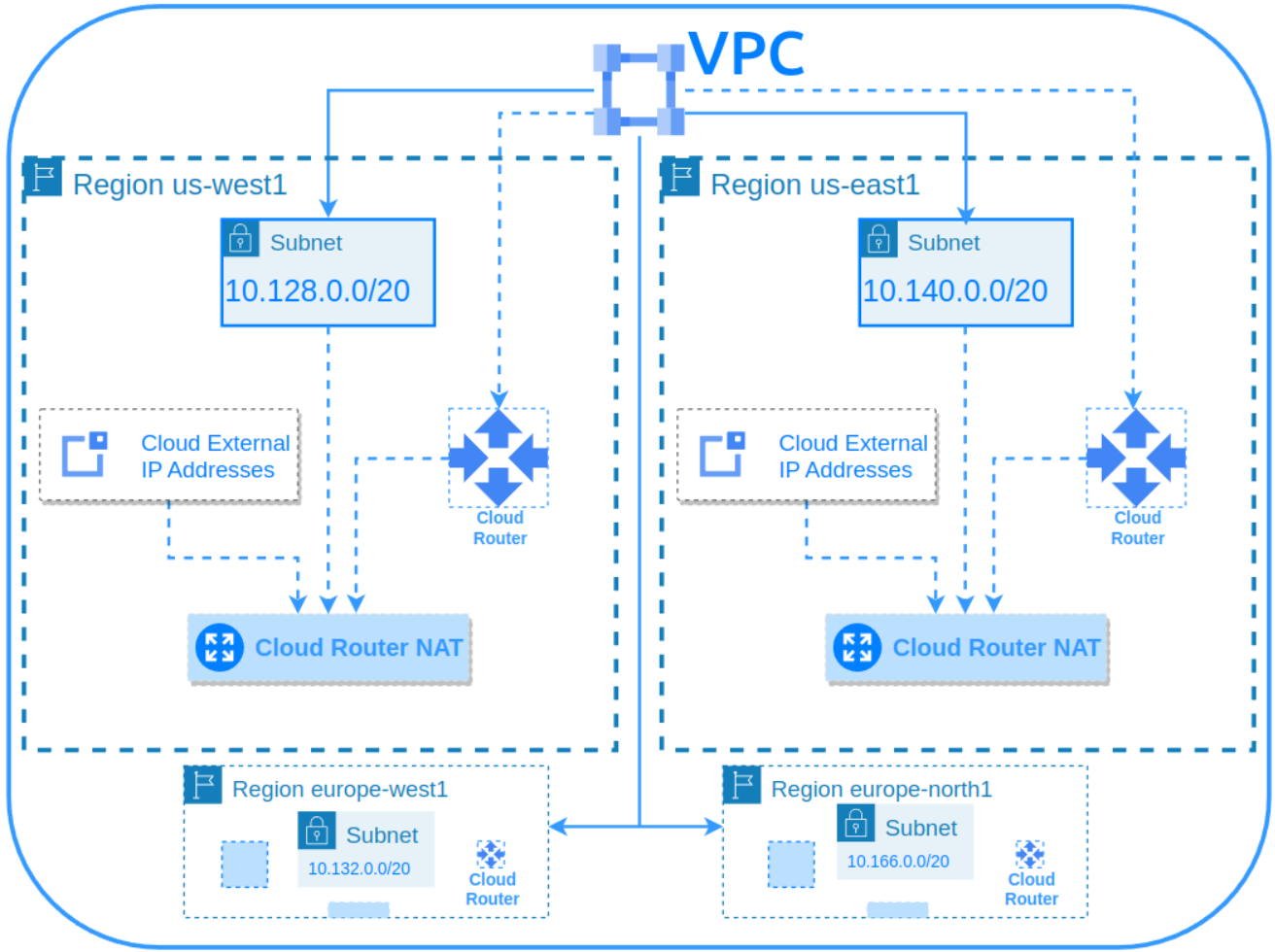
The module creates a set of resources and configures a secure multi-region/regional GCP VPC. The configuration includes subnets with Cloud NAT and external static IP address(es) in the specified region(s). Optional Private Google Access can also be enabled.
Once you have a Corewide Solutions Portal account, this one-time action will use your browser session to retrieve credentials:
shellterraform login solutions.corewide.com
Initialize mandatory providers:
Copy and paste into your Terraform configuration and insert the variables:
hclmodule "tf_gcp_vpc" {
source = "solutions.corewide.com/google-cloud/tf-gcp-vpc/google"
version = "~> 1.0.0"
# specify module inputs here or try one of the examples below
...
}
Initialize the setup:
shellterraform init
Corewide DevOps team strictly follows Semantic Versioning
Specification
to
provide our clients with products that have predictable upgrades between versions. We
recommend
pinning
patch versions of our modules using pessimistic
constraint operator (~>) to prevent breaking changes during upgrades.
To get new features during the upgrades (without breaking compatibility), use
~> 1.0 and run
terraform init -upgrade
For the safest setup, use strict pinning with version = "1.0.0"

The module creates a set of resources and configures a secure multi-region/regional GCP VPC. The configuration includes subnets with Cloud NAT and external static IP address(es) in the specified region(s). Optional Private Google Access can also be enabled.
All notable changes to this project are documented here.
The format is based on Keep a Changelog, and this project adheres to Semantic Versioning.
First stable version
In this example, module creates two subnets in different regions using only mandatory values:
hclmodule "vpc" {
source = "solutions.corewide.com/google-cloud/tf-gcp-vpc/google"
version = "~> 1.0"
name_prefix = "project-name"
subnets = {
database = {
cidr_block = "10.0.0.0/8"
region = "us-west1"
}
application = {
cidr_block = "11.0.0.0/8"
region = "us-east1"
}
}
}
In this setup, module creates three subnets with configured NAT, private GCP access and regional routes:
hclmodule "vpc" {
source = "solutions.corewide.com/google-cloud/tf-gcp-vpc/google"
version = "~> 1.0"
name_prefix = "project-name"
routing_mode = "REGIONAL"
subnets = {
database = {
nat_enabled = true
cidr_block = "11.0.0.0/8"
region = "us-west1"
}
application = {
private_access_enabled = true
cidr_block = "12.0.0.0/8"
region = "us-east1"
}
test = {
nat_enabled = true
private_access_enabled = true
cidr_block = "12.0.0.0/8"
region = "us-central1"
}
}
}
| Variable | Description | Type | Default | Required | Sensitive |
|---|---|---|---|---|---|
name_prefix |
Naming prefix for all the resources created by the module | string |
yes | no | |
subnets |
The map of specific definitions for the subnets creation | map(object) |
yes | no | |
subnets[<key>] |
subnet name | string |
yes | no | |
router_nat_logs_enabled |
Enable logging for NAT structure | bool |
true |
no | no |
routing_mode |
Network-wide routing mode to use | string |
GLOBAL |
no | no |
subnets[<key>].cidr_block |
The range of internal addresses that are owned by the subnet | string |
yes | no | |
subnets[<key>].private_access_enabled |
Specifies whether VMs in this subnet can access Google APIs and services by using Private Google Access without external IP addresses | bool |
false |
no | no |
subnets[<key>].region |
The GCP region for the subnet and related resources | string |
yes | no |
| Output | Description | Type | Sensitive |
|---|---|---|---|
subnets |
Contains attributes of created subnets | resource |
no |
vpc |
Contains attributes of google_network resource |
resource |
no |
| Dependency | Version | Kind |
|---|---|---|
terraform |
>= 1.3 |
CLI |
hashicorp/google |
~> 6.2 |
provider |