
We value your privacy
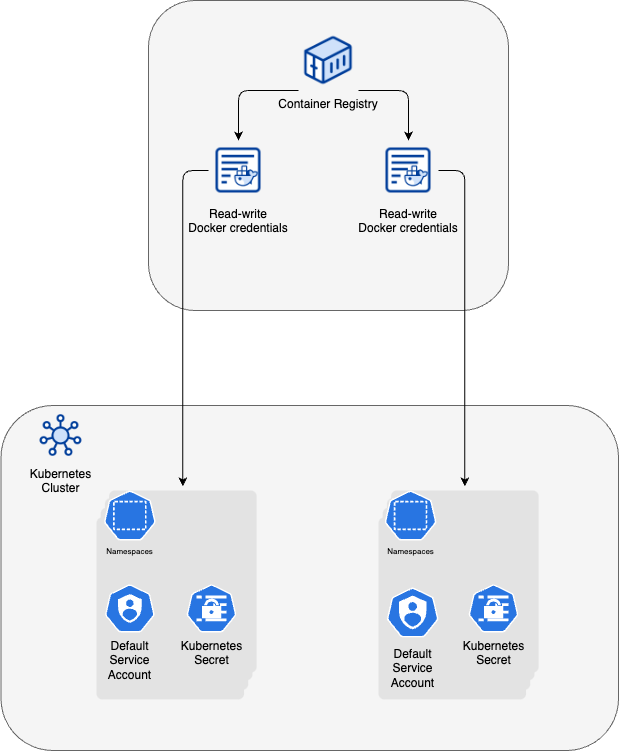
Module manages a DigitalOcean Container Registry (creates a new one or manages an existing one), creates Docker credentials to access the Container Registry with read-only and read-write permissions, and optionally configures an integration with the DigitalOcean Kubernetes Cluster namespaces.
The module is designed to wrap a DOCR resource and provide namespace-based registry authorization for DigitalOcean Kubernetes Cluster deployed by DOKS module. For the DigitalOcean Container Registry integration with Kubernetes cluster you must authenticate kubernetes provider.
Once you have a Corewide Solutions Portal account, this one-time action will use your browser session to retrieve credentials:
shellterraform login solutions.corewide.com
Initialize mandatory providers:
Copy and paste into your Terraform configuration and insert the variables:
hclmodule "tf_do_docr" {
source = "solutions.corewide.com/digitalocean/tf-do-docr/digitalocean"
version = "~> 2.0.1"
# specify module inputs here or try one of the examples below
...
}
Initialize the setup:
shellterraform init
Corewide DevOps team strictly follows Semantic Versioning
Specification
to
provide our clients with products that have predictable upgrades between versions. We
recommend
pinning
patch versions of our modules using pessimistic
constraint operator (~>) to prevent breaking changes during upgrades.
To get new features during the upgrades (without breaking compatibility), use
~> 2.0 and run
terraform init -upgrade
For the safest setup, use strict pinning with version = "2.0.1"
All notable changes to this project are documented here.
The format is based on Keep a Changelog, and this project adheres to Semantic Versioning.
kubernetes_access defaults conflicting with null valuesk8s_ro_secret_names and k8s_rw_secret_names outputs by merging them into k8s_secret_namesregion variableFirst stable version
Create only Container Registry and access credentials (for example, for integration with Docker on Digital Ocean Droplets):
hclmodule "docr" {
source = "solutions.corewide.com/digitalocean/tf-do-docr/digitalocean"
version = "~> 2.0"
name = "applications"
}
Create only Container Registry in nyc1 region and access credentials (for example, for integration with Docker on Digital Ocean Droplets):
hclmodule "docr" {
source = "solutions.corewide.com/digitalocean/tf-do-docr/digitalocean"
version = "~> 2.0"
name = "applications"
region = "nyc1"
}
Create a Container Registry and integrate it with all of the Kubernetes namespaces with the read-only permissions:
hclmodule "docr" {
source = "solutions.corewide.com/digitalocean/tf-do-docr/digitalocean"
version = "~> 2.0"
name = "applications"
kubernetes_access = {}
}
Create a Container Registry and integrate with the Kubernetes Cluster namespaces: with read-write permissions for the ci namespace and read-only permissions for all other namespaces:
hclmodule "docr" {
source = "solutions.corewide.com/digitalocean/tf-do-docr/digitalocean"
version = "~> 2.0"
name = "applications"
kubernetes_access = {
rw_namespaces = [
"ci",
]
}
}
Setup for Container Registry management in several workspaces:
hclmodule "docr" {
source = "solutions.corewide.com/digitalocean/tf-do-docr/digitalocean"
version = "~> 2.0"
create = terraform.workspace == "service"
name = "applications"
kubernetes_access = {
ro_namespaces = [
"backend",
"frontend",
]
rw_namespaces = terraform.workspace == "service" ? [
"ci",
] : []
}
}
| Variable | Description | Type | Default | Required | Sensitive |
|---|---|---|---|---|---|
name |
The name of the Container Registry | string |
yes | no | |
create |
Toggle Container Registry creation | bool |
true |
no | no |
kubernetes_access |
Parameters for granting Kubernetes namespaces access to Container Registry (set it as an empty block - {} to grant read-only permissions for all of the Kubernetes namespaces) |
object |
{} |
no | no |
kubernetes_access.ro_namespaces |
A list of namespaces that must have read-only permissions |
list(string) |
[] |
no | no |
kubernetes_access.rw_namespaces |
A list of namespace that must have read-write permissions |
list(string) |
[] |
no | no |
region |
The region slug where the Container Registry should be created in | string |
no | no | |
subscription |
The identifier for the subscription tier to use for Container Registry (starter, basic or professional) |
string |
starter |
no | no |
| Output | Description | Type | Sensitive |
|---|---|---|---|
credentials_ro |
Contains Container Registry Docker credentials with read-only permissions |
attribute |
yes |
credentials_rw |
Contains Container Registry Docker credentials with read-write permissions |
attribute |
yes |
k8s_secret_names |
Map of K8s secret names with read-only and read-write permissions in authorized namespaces | map |
no |
registry |
Contains a set of the Container Registry attributes | computed |
no |
| Dependency | Version | Kind |
|---|---|---|
terraform |
>= 1.3 |
CLI |
digitalocean/digitalocean |
~> 2.19 |
provider |
hashicorp/kubernetes |
~> 2.9 |
provider |