
We value your privacy
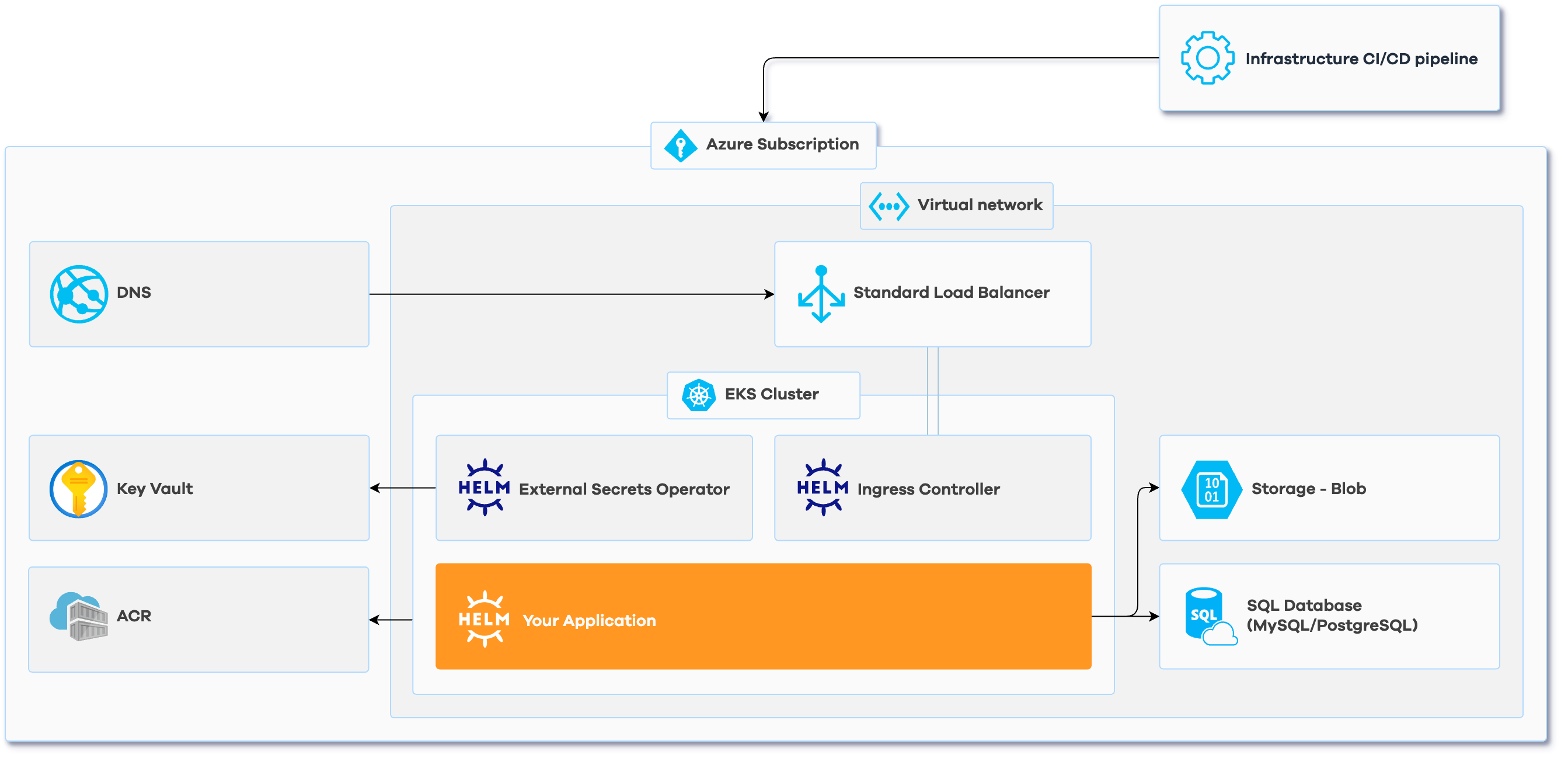
| Components | |
|---|---|
| Azure Container Registry | |
| Azure Kubernetes Cluster | |
| Azure Virtual Network | |
| Kubernetes ESO for Azure KV | |
| DNS Management |
Cloudflare
|
| Infrastructure CI/CD pipeline |
Gitlab CI
|
| Ingress Controller |
Traefik
|
| Object Storage | Blob Storage |
| SQL Database | MySQL/PostgreSQL |
| Helm Chart | |
| Setup by Corewide team | |
| Post-implementation training | |
| 2-week warranty support | |
| Documentation |
Once you have a Corewide Solutions Portal account, this one-time action will use your browser session to retrieve credentials:
shellterraform login solutions.corewide.com
Download Infrasnap archive from My Library page, unpack it to a new directory and initialize a new project there:
shellcd infrasnap/
git init
git add .
Follow the instructions in README.md:
terraform.tfvars, or using environment variables)
infrasnap.yml parameters based on the reference belowbackend.tf
Initialize the setup, create the environment you configured in infrasnap.yml and
provision
the infrastructure:
shellterraform init
terraform workspace new <environment_name>
terraform workspace select <environment_name>
terraform apply

| Variable | Description | Type | Default | Required | Sensitive |
|---|---|---|---|---|---|
cloudflare_api_token |
Cloudflare API token with DNS management permissions for all DNS zones managed in the setup. This can also be sourced from the CLOUDFLARE_API_TOKEN environment variable |
string |
no | yes |
| Variable | Description | Type | Default |
|---|---|---|---|
dns_zone_create |
Whether to create DNS zone or use the existing one | bool |
false |
dns_zone |
DNS zone in which to create records, disable to reuse the same zone from another workspace | string |
example.com |
dns_records_k8s |
A list of subdomains that must point at Ingress LoadBalancer | list |
|
dns_proxied_records_k8s |
A list of subdomains that must be proxied by Cloudflare and point at Ingress LoadBalancer | list |
|
dns_records |
List of extra records that do not point at Ingress LoadBalancer See module_docs for complete reference | map |
|
dns_records.www |
Name of the DNS record | map |
|
dns_records.www.type |
The type of the record. Possible values are: A, AAAA, CNAME, MX, NS and TXT |
string |
CNAME |
dns_records.www.value |
The content of the record | list |
['test'] |
cloudflare_account_id |
Cloudflare account ID in which to manage the DNS zone resources | NoneType |
|
cert_manager_email |
E-mail that Let's Encrypt cluster issuer will use to request certificates | string |
[email protected] |
buckets |
Buckets definitions to create | map |
|
buckets.my-bucket |
Bucket name | map |
|
buckets.my-bucket.access_mode |
Blob Storage Container (bucket) access mode. Allowed values: private, public-read | string |
private |
buckets.my-bucket.versioning |
Enable versioning for the bucket | bool |
false |
| Output | Description | Type | Sensitive |
|---|---|---|---|
name_servers |
Name servers of DNS zone managed in this workspace | attribute |
no |
bucket_names |
List of bucket names | list(attribute) |
no |